The power enjoyed by the internet today comes with threats as severe as aggressive tracking mechanisms, malware, and phishing threats, data leaks. These days, more than ever, one must put above traditional browsers that provide a numeral defense. Enter the virtual browser.
While your Chrome, Firefox, or Safari instance runs directly on your local machine, a virtual browser stands alone, light years away, in some secure environment, protecting your computer from harmful codes and preserving its anonymity while also generating unique browsing identities that cannot be traced to a common real device.
We’ll learn about virtual browsers, how they work, who needs to use them, and why they are increasingly becoming the must-haves of privacy-conscious colleges, marketers, academics, and enterprises.
What Is A Virtual Browser?
With the virtual browser, you run your browser on a remote server rather than on your own computer. As you visit sites, all the action is happening on that external server and not upon your device.
You view a mere visual image of the site while the remote system performs the execution of all code, script, and process. By design, this ensures that no bad files or trackers ever reach your local machine.
Traditional browser = runs on your laptop/phone, exposing you directly.
Virtual browser = runs remotely in the cloud, isolating you from threats.
How Does a Virtual Browser Work?
Since virtual browsers are based on a remote isolation model, they provide three types of protection to users:
- Remote Isolation: This process is virtual browsing on cloud-based servers, or a virtual machine. Your device cannot be actively involved; it only acts as a viewer.
- Visual Transmission: Only Instead of transmitting the raw code, the server streams only that “visual output” of the website while keeping malicious code far away from touching your hardware.
- Separate Digital Identities: The browsing sessions are isolated from one another, meaning the cookies, IP addresses, and device fingerprints get reset. These sites will not be able to track you from one session to the next, something that’s far more advanced than incognito or VPNs.
Benefits of Virtual Browsers
The use of a virtual browser offers a myriad of opportunities for individuals as well as companies:
- Privacy & Anonymity: Virtual browsers generate unique session IDs that the website cannot trace back to you. Ideal for avoiding profiling and targeted advertising.
- Stronger Security: Since the browser runs remotely, it acts as a shield for your local computer against malware, phishing, and illicit code execution.
- Enterprise-Grade Protection: For companies, virtual browsers provide an additional layer of compliance and mitigate the chance of employees accidentally exposing sensitive systems to online threats.
- Unrestricted Access: They will allow the safe smooth access to geo-blocked websites, empty advertisements pages, or pop-up sites without the hindrance of any speed reduction on the machine.
- Multi-Account Management: Marketers, e-commerce sellers, and researchers often need multiple browser profiles. Virtual browsers make it possible to log into different accounts simultaneously without alerting or linking.
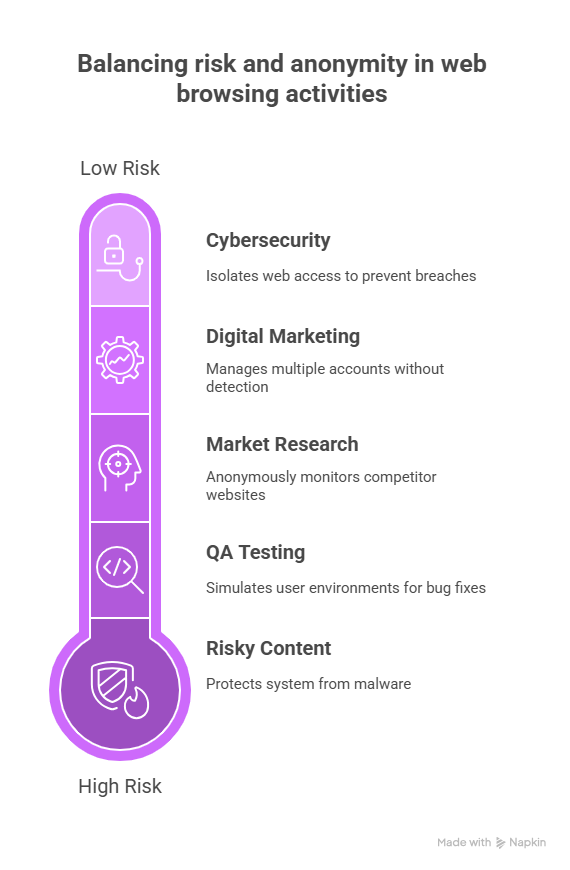
Use Cases of Virtual Browsers
Virtual browsers are not just for techies. A broad spectrum of use cases exists with them:
Digital Marketing & Ecommerce: AdsPower and GoLogin are just two examples of platforms one might use to administer advertising campaigns and handle many accounts at once, without the web services blocking them.
Market Research & Competitive Intelligence: Analysts bear witness to competitor sites under the umbrella of anonymity.
QA & Web Testing: To fix a user-identified bug, the tool is used in test environments to see the website on various browser/device combinations.
Enterprise Cybersecurity: With the help of VirtualBrowser and other such solutions, web access for users is isolated so that a breach is prevented.
Checking Out Risky Content: Be it researching dark web or malware-infested sites, this way ensures users don’t expose their personal systems to risks.
Who Should Use a Virtual Browser?
Virtual browsers are not just for IT pros—they come with a wide apparatus of tools for a wider variety of users. Here are those groups who are the biggest beneficiaries:
Privacy-Conscious Individuals: A virtual browser is one of the best tools if you want to browse without leaving any digital footprints. In contrast with VPNs or an incognito mode, it completely isolates your identity and by this, tracks cannot be carried out between sessions.
Marketers and E-Commerce Sellers: With multiple advertising accounts on some platforms, such as Facebook and Google Ads, there runs big risks of being banned due to account linking. Virtual browsers like AdsPower and GoLogin enable marketers to generate safe browser profiles separated for each account.
Researchers and Analysts: Journalists, academics, or competitive intelligence representatives usually need to collect data without revealing the real IP or device fingerprint. The virtual browser will keep the research under wraps.
Followed by enterprises and security teams: Organizations with strict compliance requirements keep enterprises, their remote isolation ensuring that no harmful code reaches the corporate network, to virtual browsers for protection from phishing, malware, and risky sites.
Virtual Browsers vs. VPNs and Incognito Mode
While many people use VPNs or incognito mode for privacy, virtual browsers offer a fundamentally different and often more secure approach. Let’s compare the key differences.
| Feature | Virtual Browser | VPN | Incognito/Private Mode |
|---|---|---|---|
| What it does | Runs browser on a remote server, isolating your device from the internet. | Masks your IP address and encrypts your internet traffic. | Deletes your local browsing history, cookies, and site data after the session ends. |
| Security | Excellent. Protects your device from malware, phishing, and malicious code because all execution happens remotely. | Good. Protects data in transit from snooping and tracking. | Weak. Offers no protection against malware or website tracking. It only hides activity from other users of your device. |
| Privacy | Excellent. Creates a new, unique digital identity for each session (new IP, cookies, device fingerprint), making cross-session tracking nearly impossible. | Good. Hides your real IP, but websites can still track you using other data (e.g., cookies, device fingerprint). | Weak. Does not hide your IP or device fingerprint. Websites can still track you within and across sessions. |
| Performance | Can have a slight delay since you’re streaming a video feed of the browser. | Generally, it can slow down your connection speed due to encryption. | No impact on performance. |
| Best for | – Secure access to risky sites – Multi-account management – Market research – Enterprise security |
– Hiding your IP address – Accessing geo-restricted content – Securing public Wi-Fi |
– Hiding browsing history from family members – Quick, temporary searches |
| Main Limitation | Not all providers are equal; can be a paid service. | Not a full security solution; doesn’t protect from browser-based threats. | Gives a false sense of security. |
Conclusion
With days going by, the outdated internet browsers were no longer considered enough to provide true online privacy and security. Virtual browsers stand by the user by running remotely to protect him from malware and to establish different digital personalities for each session.
A virtual browser offers a secure, versatile hearing environment for the marketer juggling many accounts; for the researcher who often undertakes sensitive inquiries; and for the company that needs to keep its workers’ identities secret.
Going forward, though, as cybersecurity issues continue to rise, virtual browsers are bound to become the core technology for safe internet use.