Enabling Remote Desktop across multiple computers has become a routine requirement in many workplaces. Walking from desk to desk to switch it on might be fine for a handful of machines, but once you’re managing dozens, or even hundreds, it’s no longer practical. That’s where Group Policy comes in. Built into Windows Server, it gives administrators a centralized way to turn on Remote Desktop and keep settings consistent across the network. In this piece, I’ll break down how it works and why it’s often the most efficient way to manage remote access.
Here’s the quick recap:
- Open Group Policy Management
- Create and edit a new GPO
- Enable Remote Desktop under Connections
- Open the firewall rule
- Apply and test
Now let’s break that down in detail.
Prerequisites (Before You Start)
Before diving in, make sure these boxes are checked:
- Active Directory in place: Group Policy only works in an AD environment, so your PCs need to be joined to the domain.
- Admin rights: You’ll need administrative privileges to create or edit Group Policy Objects (GPOs).
- Firewall rules: Remote Desktop requires that the firewall allows RDP traffic , don’t worry, we’ll cover how to enforce this later.
Once you’ve got those sorted, you’re ready to configure.
Enable Remote Desktop via Group Policy: Step-by-Step Guide
Step 1: Open Group Policy Management
On your domain controller (the server that manages network policies):
- Press
Win + R, typegpmc.msc, and press Enter. - If that doesn’t work, add the Group Policy Management feature in Server Manager → Add Roles and Features.
Expand your domain tree in the left panel.
Pro tip: Test first. Don’t roll this out to your entire domain until you’ve tried it on a test Organizational Unit (OU) with just a couple of PCs. Troubleshooting in a sandbox is much easier than fixing dozens of machines.
Step 2: Create or Edit a GPO
Decide where you want this policy to apply:
-
Right-click the domain or the OU.
-
Choose Create a GPO in this domain, and Link it here…
-
Give it a clear name like Enable Remote Desktop.
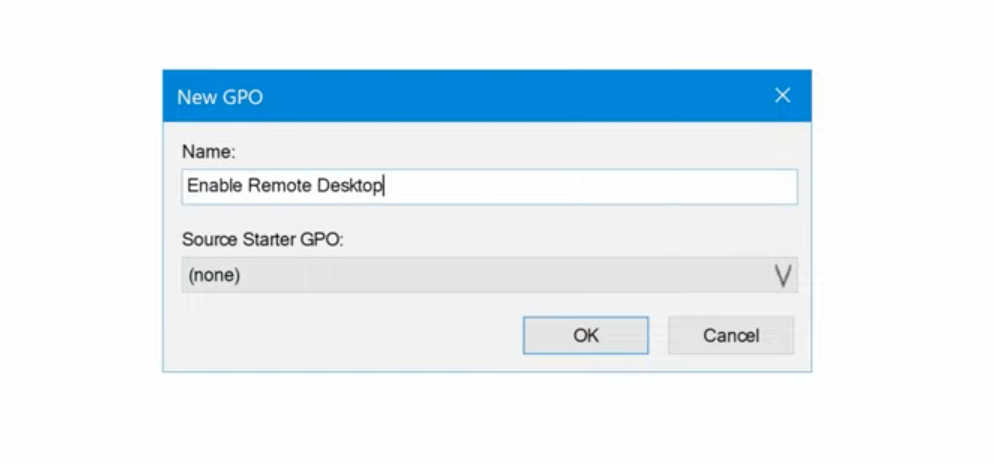
-
Once it appears, right-click it and choose Edit.
Step 3: Turn On Remote Desktop
-
Inside the Group Policy editor, navigate to:
Computer Configuration → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Session Host → Connections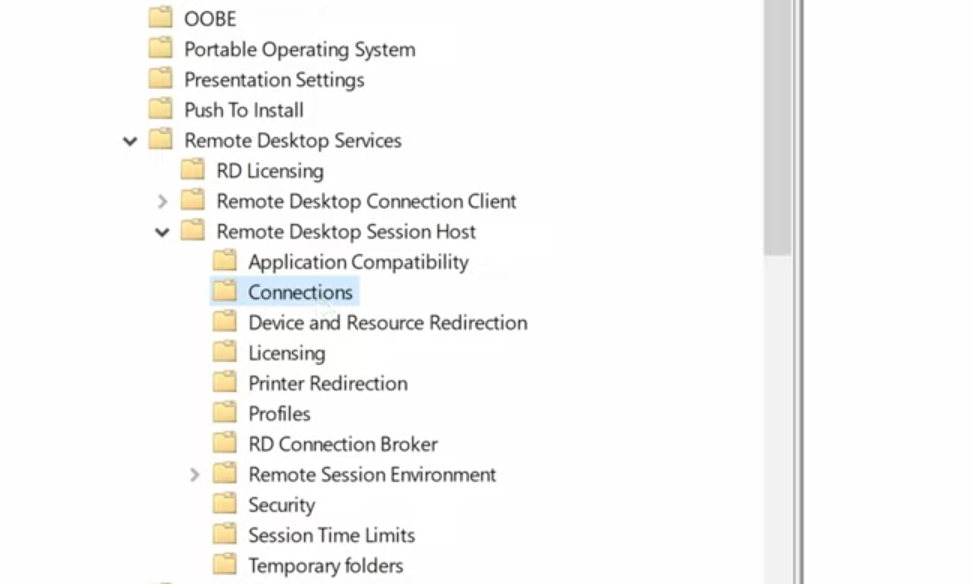
-
Double-click Allow users to connect remotely using Remote Desktop Services.
-
Set it to Enabled and click OK.
This is the switch that actually allows RDP connections.
Step 4: Make Sure the Firewall Allows It
-
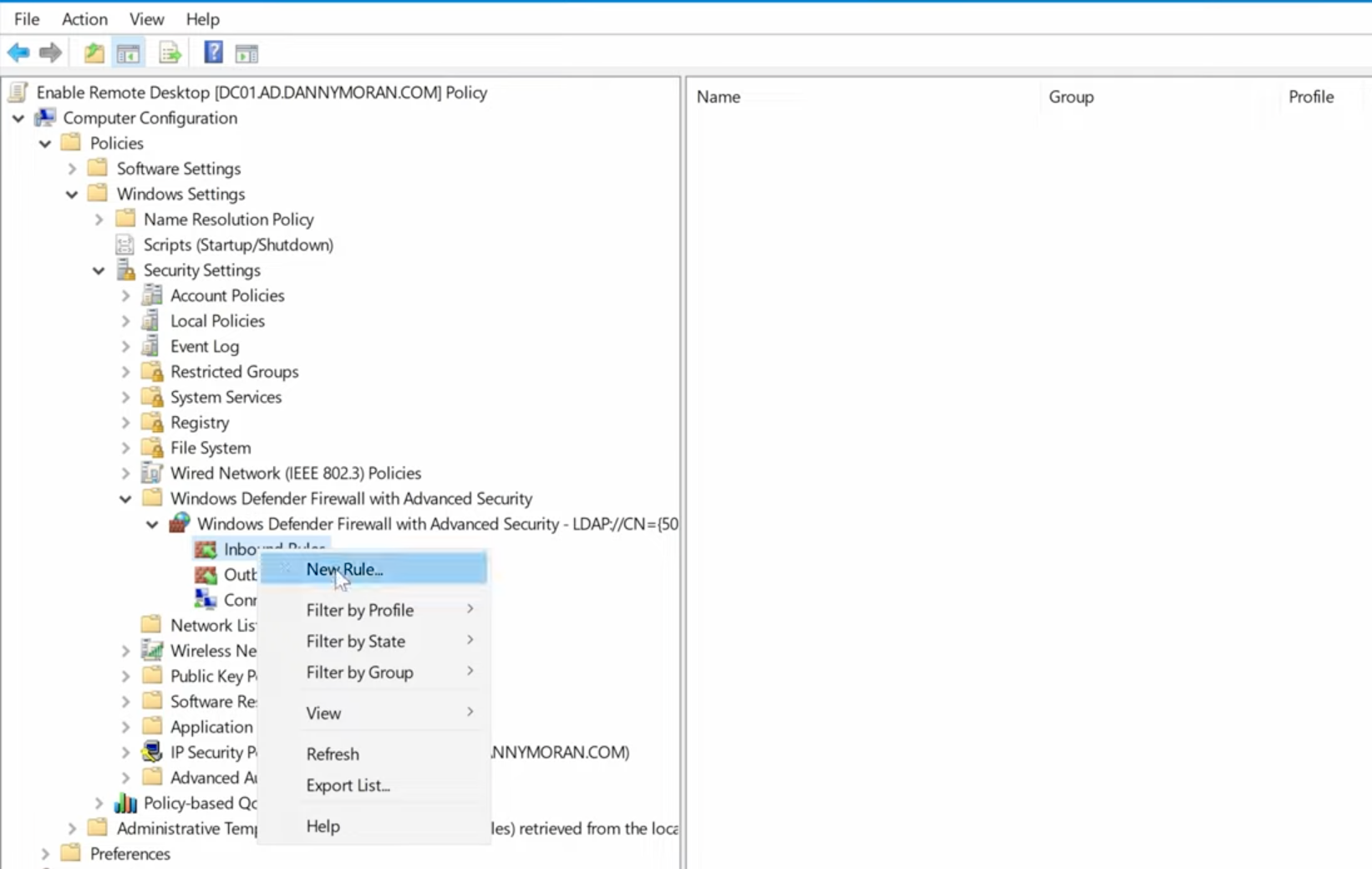
Remote Desktop won’t work if the firewall blocks it. In the same GPO editor, go to:
Computer Configuration → Windows Settings → Security Settings → Windows Defender Firewall with Advanced Security -
Under Inbound Rules, look for Remote Desktop – User Mode (TCP-In) and set it to Enabled.
-
You may also see a UDP-In rule for Remote Desktop, enabling that too for the best performance.
Step 5: Apply the Policy
Group Policy refreshes on client machines automatically (about every 90 minutes with a random offset). But if you want it right away:
On the client PC, open Command Prompt and run:
gpupdate /force
If everything is configured correctly, RDP should now be live and ready to use.
Troubleshooting Tips
Even when you follow the steps perfectly, a few things can still trip you up. Here’s what I’ve run into in the field:
- “Remote Desktop can’t connect” errors → Nine times out of ten, it’s either the firewall or a network routing issue. Double-check that the firewall rule applied.
- Users can’t log in → By default, only administrators can log in via RDP. If you want regular staff to connect, add them to the Remote Desktop Users group on the target machine.
- The GPO isn’t applying → Run
gpresult /rfrom a client PC. If your GPO doesn’t show up, check whether the PC is in the right OU and whether the GPO is linked properly.
Security Best Practices (Don’t Skip This Part)
RDP is convenient, but it’s also a favorite target for attackers. I’ve seen environments get hammered by brute-force attempts simply because RDP was wide open. Here’s what I always recommend:
- Enable Network Level Authentication (NLA). It forces authentication before a full session is established.
- Limit RDP access to trusted IP ranges if possible.
- Require strong passwords (and ideally multi-factor authentication if your setup supports it).
- Monitor event logs for failed login attempts.
And if users are connecting from outside the office, strongly consider putting RDP behind a VPN. It’s an extra layer, but it pays off big time in terms of security.
Wrapping It Up
Enabling Remote Desktop with Group Policy is one of those tasks that feels intimidating at first but quickly becomes second nature. Once you’ve done it once, you’ll never go back to manually clicking through System Properties on every machine.
Do this once, and you’ve got RDP rolled out consistently across your network. No more guessing which machine is set up right, no more half-working connections. Just clean, reliable access everywhere you need it.